Windows comes by default, with a fair amount of security. However, there are a few goodies installed or configured on your computer that are used for marketing and other statistical purposes. A lot of people would consider this data gathering as an invasion of privacy. Below are a few simple methods that will help prepare for a system failure, preserve your privacy and reduce the chances of a cyber attack.
One of the many realms of security is restoration. Windows 10 gives you the ability to restore your system in case things go south during maintenance or an install that went wrong. If your computer crashes, you can restore your computer back to where it was when you created the restore point.
- In the search box on the taskbar, type "Create a restore point", and select it from the list of results.
- On the System Protection tab in System Properties, select Create.
- Type a description for the restore point, and then select Create, then OK.
- Click here to see how to restore from a restore point.
This basically takes a snapshot of your computer settings. If an event such as installing software or hardware causes a system failure, you can restore your settings from this snapshot.
Keep in mind that this does not take place of a backup.

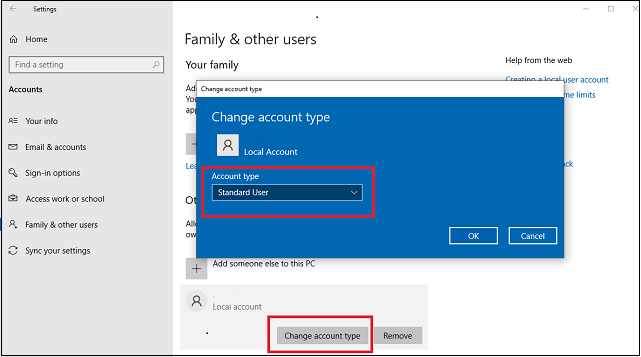
By default, the account created when you first login is given Administrative (full access) rights to the computer. This can be dangerous in the event the account is compromised. It is recommended that you create a user account without Administrator access for daily use. The Administrator account should only be used when making modifications to the system or installing software. You don't want to be surfing the Internet using an account that has administrative rights to your computer. To view your accounts, follow the steps below.
- Right click Start and select Settings. Click on accounts.
- Click "Family & Other Users to see a List of local accounts.
- Click on a user to view or change the account type. Most accounts should be set to "Standard User".
By default, Microsoft OS comes with the ability to track your location and online behavior for marketing purposes. They collect your information and is used to sell advertising. This can be turned off within settings.
- Go to Start, then Settings.
- Click on the Privacy icon.
- Click on Location and then click the on-switch icon to turn location tracking off. This will turn off the tracking feature.
- In the Privacy settings, turn off the setting for "Let apps use advertising ID" and "make ads more interesting to you based on your activity".
- You can turn off Camera access but this may affect web-conferencing apps. Here you can select which apps can access your camera.

Passwords seem like a simple thing but they are usually the weakest line of defense. Hackers have many tools that are used to guess your password. Make sure you follow the proper methods. Passwords are the keys to your castle.
- Use a complex password.
- Never use one password for all systems.
- Use a password vault.
- Use Multi-Factor Authentication when possible.
- Never share your passwords.
- More on passwords.
Windows 10 comes with a pretty solid Anti-virus and Firewall component. As part of the Windows Defender Security you can modify these tools which by default are activated. Please note that it is recommended that you do not have two firewalls and/or Anti-Virus programs running as they can work against themselves. For instance, If you are using Windows Anti-virus, you should not also be running Norton Anti-virus. You can change or view the settings.
- In the search bar type "Control Panel", then click System and Security.
- Click "Windows Defender Firewall".
- Here you can view the status of your firewall.
- Click "Turn Windows Defender Firewall on or off" on the left panel if you need to change it.

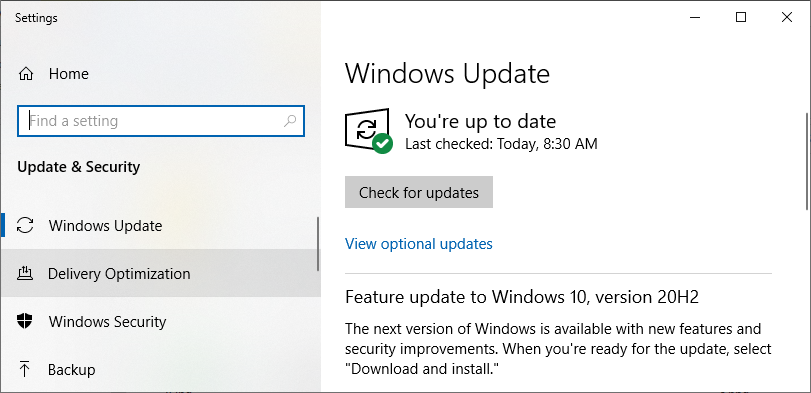
One of the easiest ways to protect your system is to make sure all of your drivers and software are up to date. As time goes by, attackers discover vulnerabilities in software. Once they are discovered, they are quickly published by the software companies to warn people. Unfortunately they are counting on users to update the software before attackers read and exploit the vulnerability. There is an automated process but for peace of mind, you can run this manually.
In most instances of malware infection, the malware can operate only using the privileges of the logged-in user. To minimize the impact of a malware infection, consider using a standard or restricted user account such as a non-administrator account for day-to-day activities. Only log in with an administrator account—which has full operating privileges on the system—when you need to install or remove software or change your computer’s system settings.




